The Next Mobile Defense Challenge: Protecting Cloud-Native Networks
Sat, 24 Jul 2021 15:24:52, atika, [category: 5g-community]
SRLabs Achievement
SRLabs have been finding security issues in a mobile network for over a decade, and regularly help to fix them. Below is the symbiosis of mobile network hacking research and risk management for mobile network operators.
Today’s Mobile Networks are Built from Secure and Insecure Protocols
Baseline Telco Standard from 2G the security level is a major hacking issue. Then from 3G until 5G Baseline Telco Standards the security level believed to be secure.

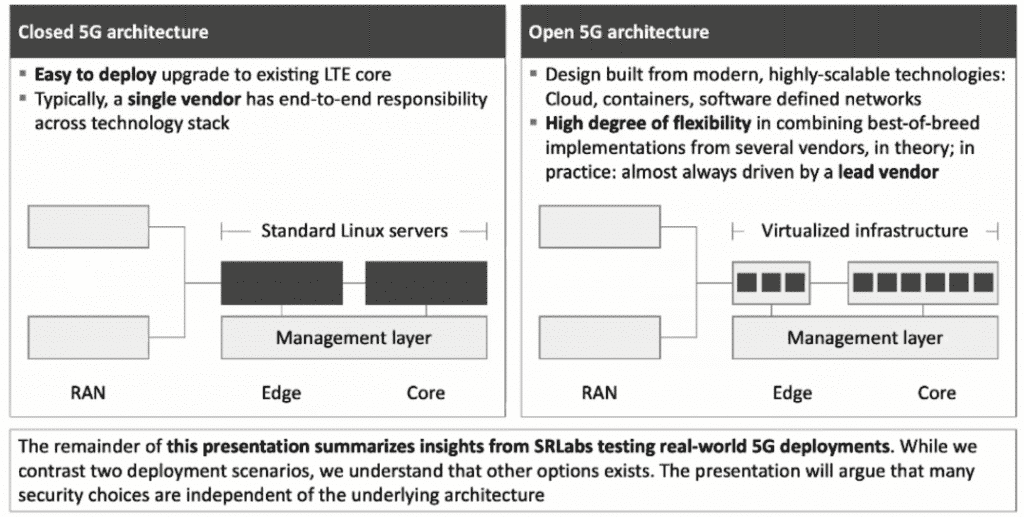
Telcos are Facing a Choice Between Closed and Open 5G Architecture
This presentation summarizes insights from SRLabs testing real-world 5G Deployments. SRLabs contrast 2 deployment scenarios, and they understand that other options exist. There are many security choices that are independent of the underlying architecture. The difference between Closed 5G architecture and Open 5G architecture.
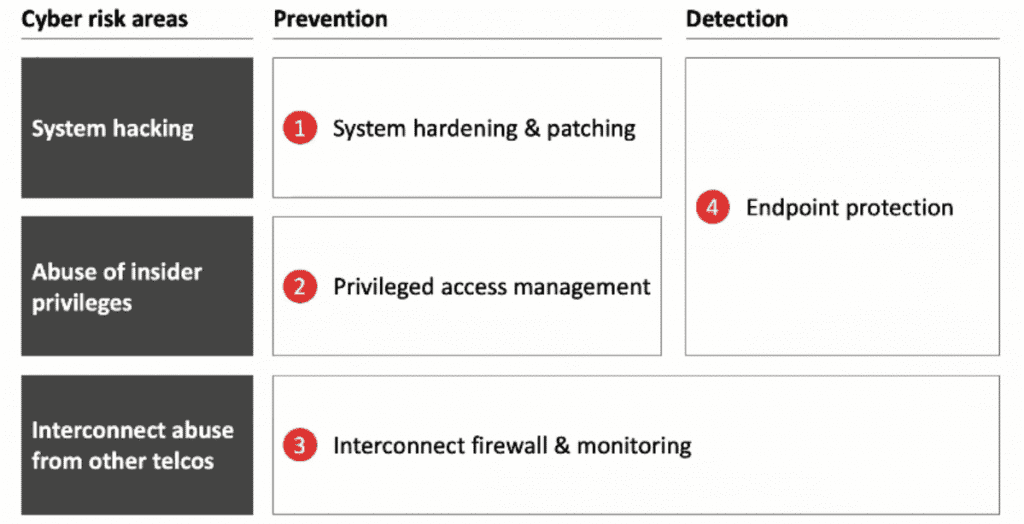
Successful Telco Cyber Defence Focuses
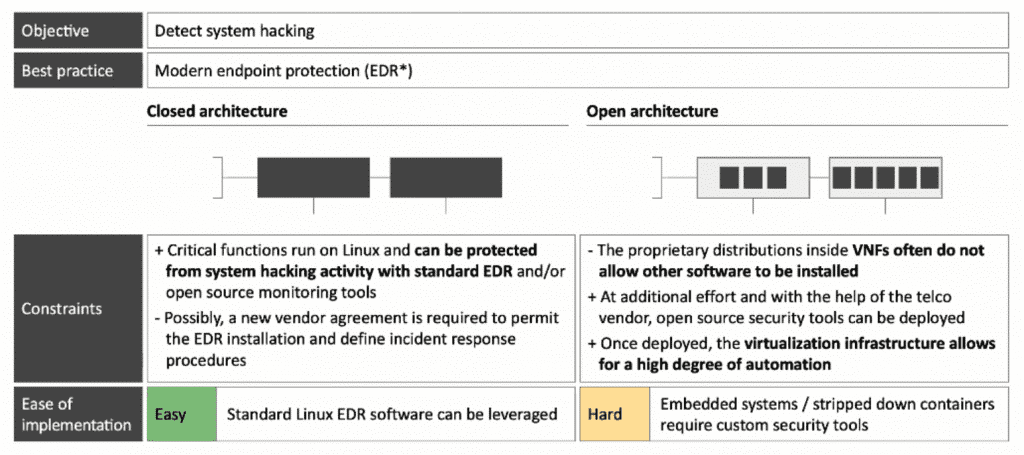
Successful Telco Cyber defence focuses on prevention and detection across 3 key risk areas, there are: System hacking, abuse of insider privileges, and interconnect abuse from other Telcos. The figure below is an example of defence best practices to make you more understanding.
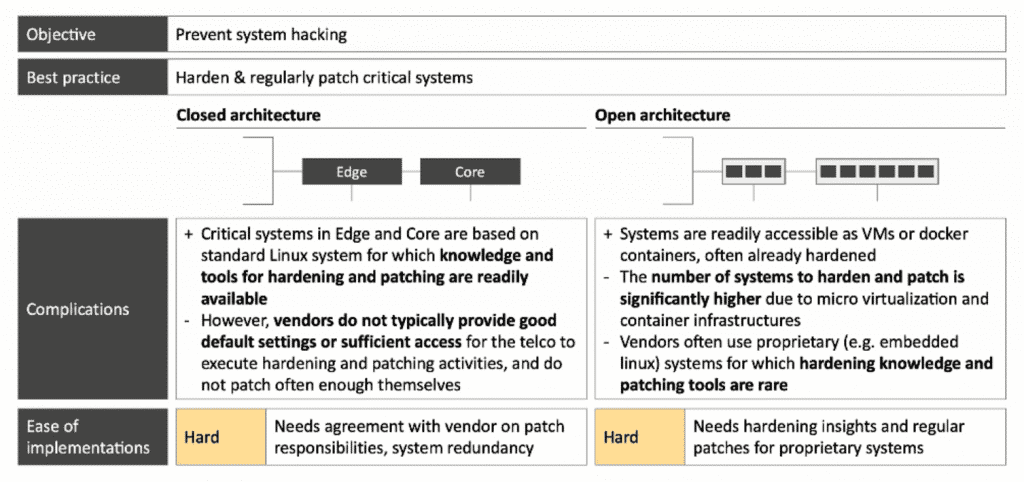
1. System Hardening & Patching
Adequate system maintenance is hard in both Telco architectures, but for different reasonsThe objective is to prevent system hacking and the best practices are to harden and regularly path critical systems. Closed Architecture and Open Architecture are relatively hard to solve. The table below the differentiations between Closed Architecture and Open Architecture based on the complications and the ease of implementation.
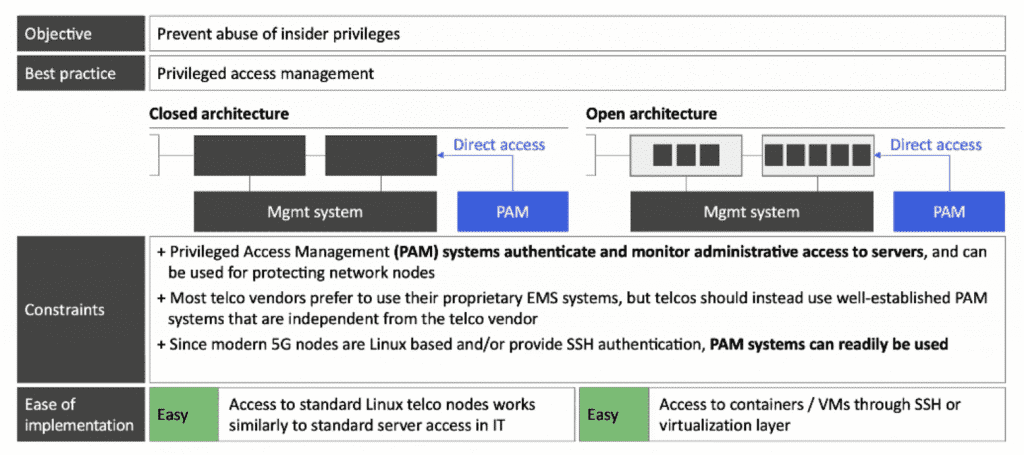
2. Privileged Access Management
Standard PAM system can protect core network nodes from rogue/hacked insiders. The objective is to prevent abuse of insider privileges and the best practice for this is privileged access management. Both architectures are relatively easy to solve. The closed architecture needs access to standard Linux Telco nodes that works similarly to standard server access in IT while the open architecture needs access to containers/VMs through SSH or the virtualization layer.
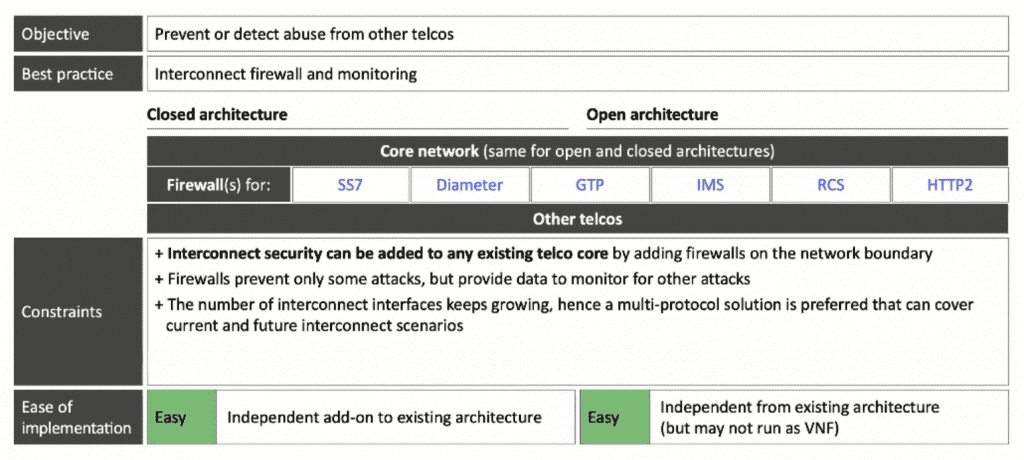
3. Interconnect Firewall & Monitoring
Interconnect protection can and should be added to any Telco core. The objective is to prevent or detect abuse from other Telcos and the best practice is to interconnect firewalls and monitoring. Those architectures are relatively easy to solve. The closed architecture only needs independent add-on existing architecture and the open architecture need the independent from existing architecture (but may not run as VNF).
4. Endpoint Protection
Modern endpoint protection can be deployed easily on standard Linux, but not on many VNFs in open network architectures. The objective is to detect system hacking and the best practice for this is a modern endpoint protection (Endpoint Detection and Response or EDR). For closed architecture relatively easy to solve but for open architecture is relatively hard to solve. The table below the differentiations between Closed Architecture and Open Architecture based on the complications and the ease of implementation.